Configuration to use client browser to access the platform's web UI
The Platform as a Service provides multiple Web Interfaces to monitor the state of the platform, your workloads as well as interact with your datasets. Although these Web Interfaces can be accessed by using the platform acces servers's browser using X forwarding, you might want to configure your local device for faster interactions. This page describes the configuration procedure to access the platform services' web UI using the browser on your local host for Debian or fedora based linux distributions.
Required packages
The platform is secured using MIT Kerberos authentication. To use your machine's browser to access the platform, you will have to install client package to authenticate against the platform.
| Operating system | package installation command |
|---|---|
| Ubuntu/Debian | sudo apt-get install krb5-user |
| Fedora/Centos/RedHat | sudo yum install krb5-workstation |
Connection to the platform & Kerberos configuration
Authentication request forwarding
Acces to the Web User interfaces require user authentication. This is done by interactiong with the platform Kerberos server. The Kerberos server is not directly accessible from outside the platform. To access it you will have to use ssh forwarding. To do so you will have to choose an available port on your machine. Let's choose, for example, the port number 9571. To enable forwarding needed for Kerberos authentication request, you need to use the following command :
ssh -L 127.0.0.1:9571:lsd-prod-krb-1.lsd.novalocal:88 <username>@147.210.117.54
This command will redirect request made to the chosen port on your local host to the server where Kerberos is located(lsd-prod-krb-1.lsd.novalocal)
Kerberos configuration
You will need to configure the local Kerberos client by modifiying its configuration file /etc/krb5.conf In this file, you will find two sections called [realms] and [domain_realm]. Please add the content indicated below to theses sections. Make sure you use the same port number as in your ssh connection cammand.
[realms]
LSD.NOVALOCAL = {
kdc = 127.0.0.1:9571
admin_server = 127.0.0.1:9571
}
[domain_realm]
.lsd.novalocal = LSD.NOVALOCAL
lsd.novalocal = LSD.NOVALOCAL
Authentication
To issue an authentication request, use the kinit command.
kinit <username>@LSD.NOVALOCAL
Provided that you give the correct password, this will grant you a Kerberos ticket authenticating you against the plateform. This ticket will stay valid for 24 hours. A similar ticket is automaticaly provided on the platform gateway(147.210.117.54)
Firefox browser configuration
Configuration for Kerberos authentication
Firefox needs to be configured to use the Kerberos authentication to access the platform's interfaces. To do so , you need to acces firefox's configuration using the url about:config and modify the following properties
| property | value |
|---|---|
| network.negotiate-auth.trusted-uris | .lsd.novalocal |
| network.negotiate-auth.delegation-uris | .lsd.novalocal |
SOCKS Tunneling
The platform servers being only accessible throught 147.210.117.54, you will need a SOCKS tunnel to enable access to the webUI from your client computer. To do so, you need to choose an available port on your machine and enable application port forwarding using ssh -D option. Combining with the ssh forwarding needed for Kerberos authentication and using 7777 as an example port, the command used to connect to the platform becomes :
ssh -D 7777 -L 127.0.0.1:9571:lsd-prod-krb-1.lsd.novalocal:88 <username>@147.210.117.54
Next you will need to configure your browser to send request to the platform throught the SOCKS proxy.
*Search 'proxy' in firefox's preferences
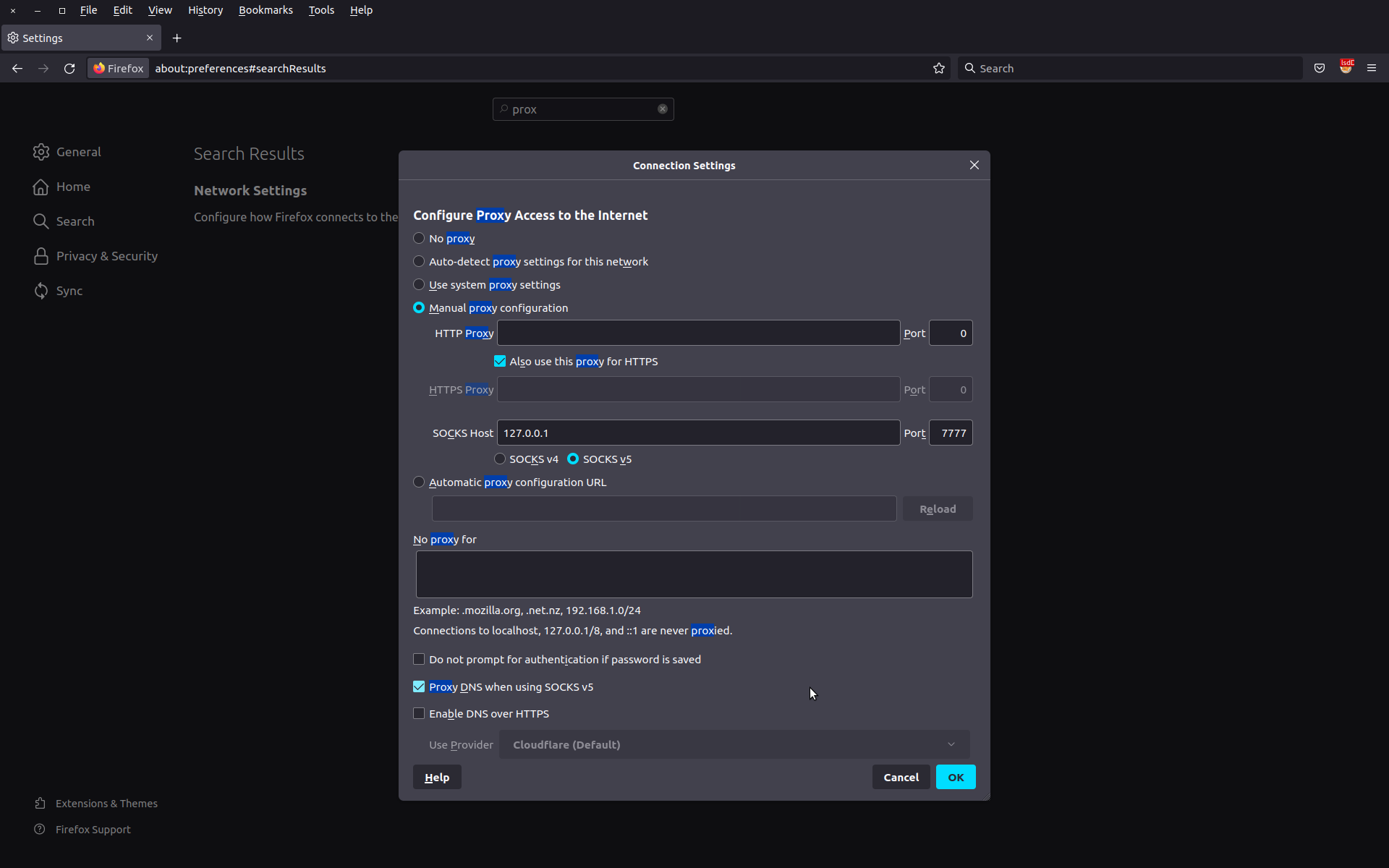
*Configure the proxy with the choosen port. Use the same proxy for all protocol and configure the proxy to issue DNS requests throught the proxy
Some firefox add-ons like FoxyProxy also use up the use of such proxies.
Configure client ssh
Instead of using the previous command line to connect to the PaaS, you might opt to pre-configure an alias using you local host ~/.ssh/config file. The following configuration (to be added to ~/.ssh/config file) will help setting up connection to the paas
Host lsdProxy
User <username_lsd>
HostName 147.210.117.54
LocalForward 127.0.0.1:9571 lsd-prod-krb-1.lsd.novalocal:88
DynamicForward 7777
Using this configuration, the alias lsdProxy can be used to connect to the paas acces node(147.210.117.54), while setting up SOCKS Tunneling (DynamicForward) and authentication tunnel(Local forward)
ssh lsdProxy
Port 7777 is the port you configured as your web proxy in your browser. Port 9571 is the port you specified in your kerberos configuration.

